Home | Peek Electronics | Peek Fireworks | Peek Helicopters | GCHQ Competitions | Enigma Machines
2011 Can You Crack It | 2013 Can You Find It | 2014 Cyber Security Challenge | 2015 - 2016 Christmas Card Puzzle | 2016 - 2017 The GCHQ Puzzle Book | 2018 - 2019 The GCHQ Puzzle Book II
Christmas Tree & Wine Glass Challenge | Alan Turing Cryptography Challenge | GCHQ Minority Reports | Alan Turing £50 Note Puzzle
GCHQ Can You Crack It 2011 (Stage 1)
The three stages within
the challenge are designed so that participants can demonstrate the
basics of analysing shellcode and obfuscation mechanisms, reverse
engineering of malicious binary code and vulnerability analysis. These
techniques are fundamental skills for a cyber security specialist at
GCHQ
This starts with the main image on the canyoucrackit.co.uk
site. To solve this stage it is necessary to identify that this is code
that can be run by an Intel x86 compatible processor. After analysis, it
is clear that this machine code implements the RC4 decryption algorithm,
and is able to decrypt a block of data that is hidden inside the PNG
file, in a comment tag. Once decrypted, this data reveals the location
of stage 2 of the challenge.
Solved by
Dr Gareth Owen
School of Engineering
University of Greenwich
Click on Image for more information.
Senior Lecturer
School of Computing
University of Portsmouth
Can You Crack It Stage 1 Part 1
![]() Can You Crack It Stage 1 Part 1
Can You Crack It Stage 1 Part 1
Can You Crack It Stage 1 Part 2
![]() Can You Crack It Stage 1 Part 2
Can You Crack It Stage 1 Part 2
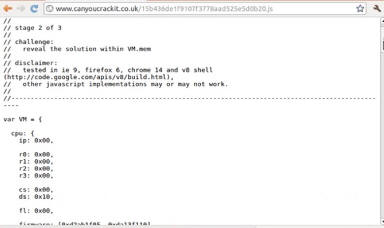
GCHQ Can You Crack It 2011 (Stage 2)
This is a JavaScript programming challenge, with a cyber security angle. To solve this stage an implementation of a simple virtual processor is required. Some notes on the architecture are provided along with a block of data that can be analysed. Solving this stage will reveal the final stage of the challenge.
Can You Crack It Stage 2
GCHQ Can You Crack It 2011 (Stage 3)
The final
stage is a reverse engineering challenge. An executable file can be
downloaded from the location revealed in stage 2. This executable parses
a license file - if it gets given a correct input, the challenge is
revealed to be over, and a link to the 'success' page is provided to the
participant.
We included a number of ways that this stage could
be solved, as we are interested to see how people would attack the
problem - coming up with innovative solutions to seemingly impossible
problems is the day job at GCHQ. For example, there has been some
comment by security experts on the fscanf buffer overflow that we
included in this executable - one option to solving the problem would be
to use this overflow to skip over certain checks in the executable.
Other alternatives for this stage involved breaking the weak crypt,
patching the executable directly to bypass the check, or analysing the
assembly instructions and realising that this was all a complete
diversion.
Can You Crack It Stage 3
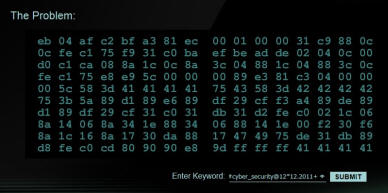
This website address will revel the Key:
Pr0t3ct!on#cyber_security@12*12.2011+
Enter Keyword at http://www.canyoucrackit.co.uk click submit.
You will then be redirected to URL:
http://www.canyoucrackit.co.uk/soyoudidit.asp
___________________________________________________________________________________________________________________________________________________________________________________________________________